clusterissuer Setup Guide
This guide will walk you through setting up clusterissuer, certificate management for Kubernetes.
Prerequisites
- [Cert-Mananger[(/guides/#cert-manager) and [Prometheus(-crds)]((/guides/#prometheus)
Configure ACME Issuer
You can setup multiple domains and/or DNS providers with a single clusterissuer app.
Cloudflare DNS Provider
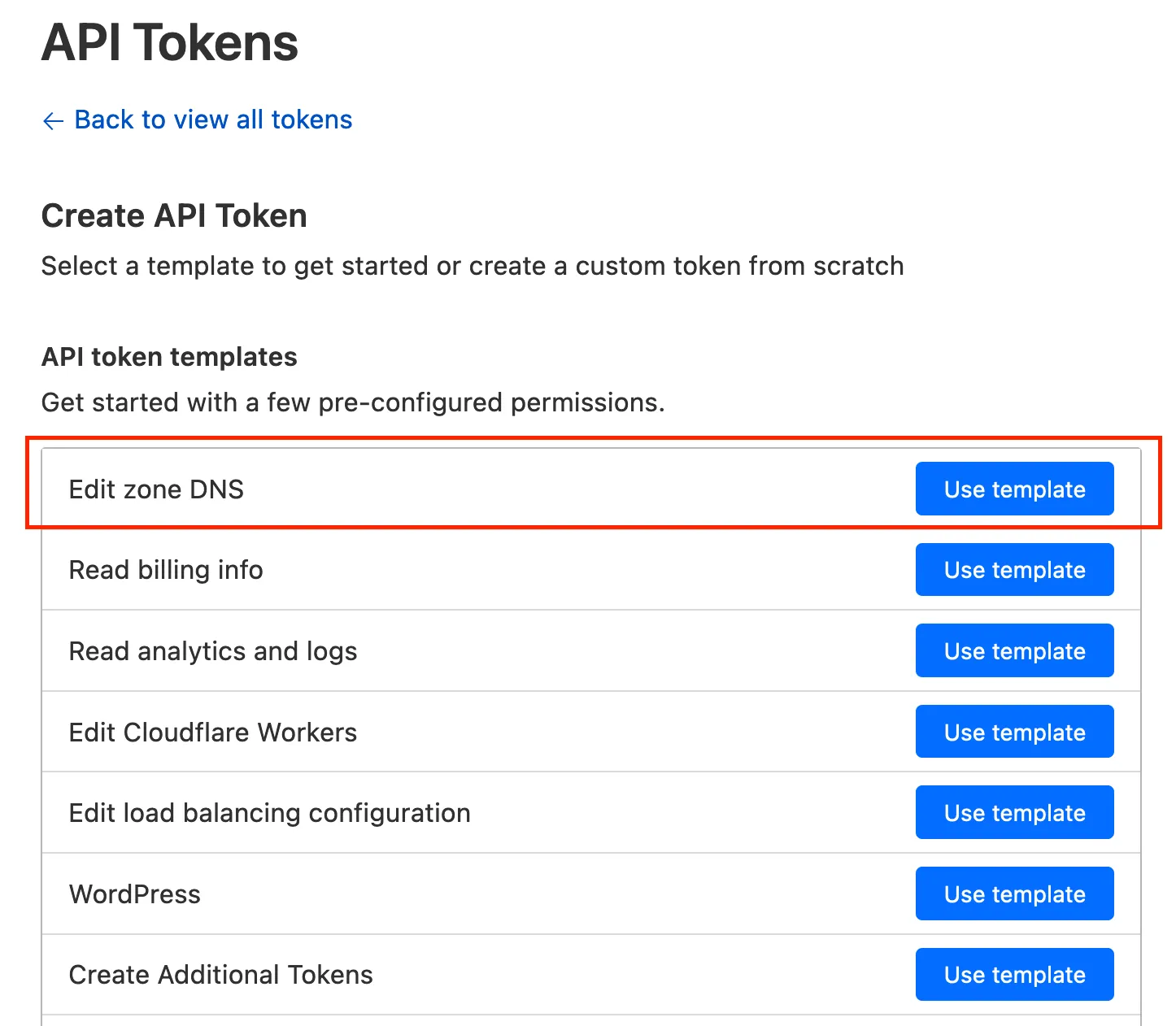
Create a Cloudflare API token
Login to Cloudflare dashboard and go to the Cloudflare API Tokens page. Select Edit Zone DNS template.
The recommended API Token permissions are below:
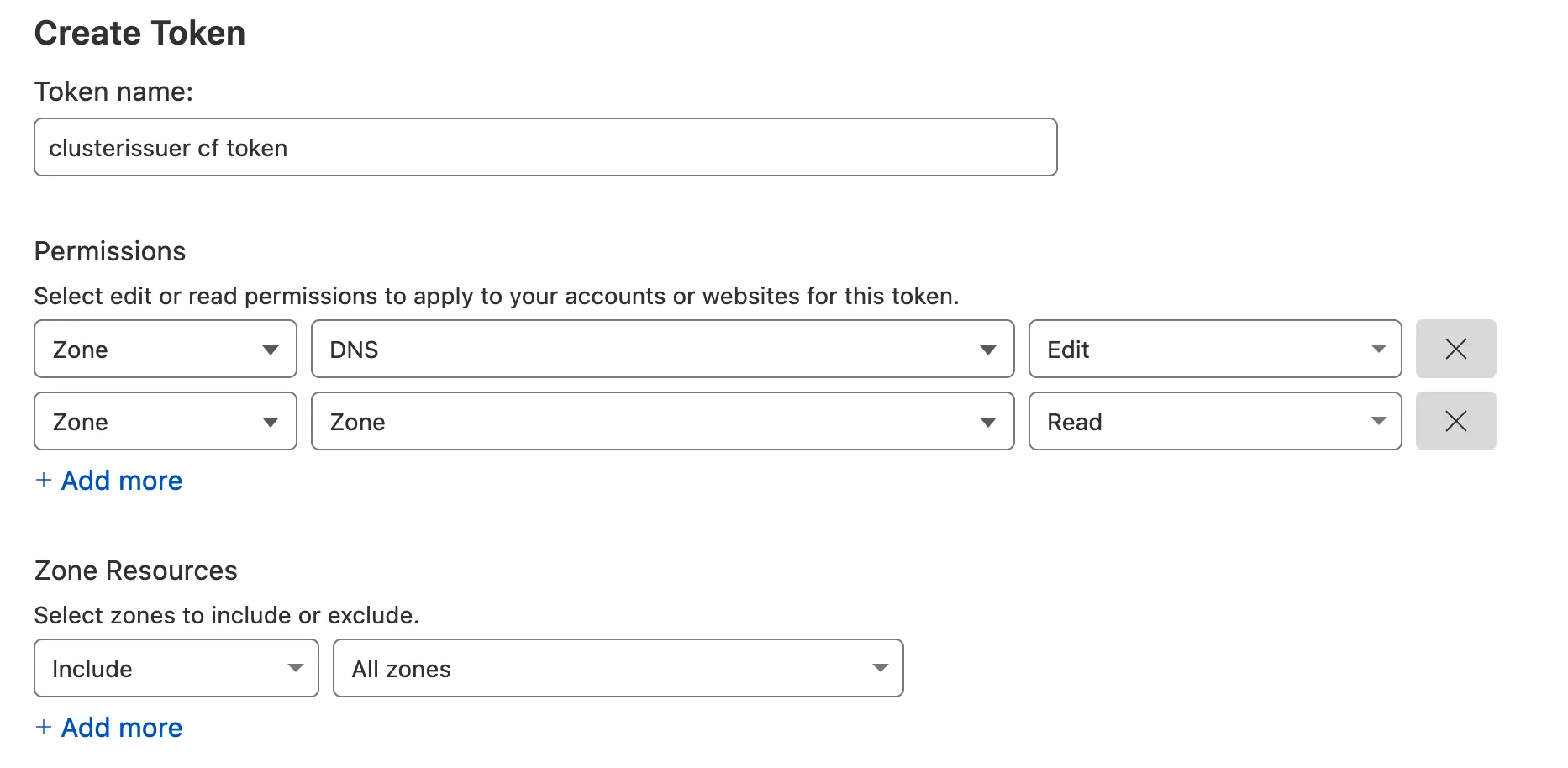
Cloudflare ACME Issuer Settings
clusterIssuer: ACME: - name: domain-0-le-prod # Used for both logging in to the DNS provider AND ACME registration email: "${DOMAIN_0_EMAIL}" server: 'https://acme-staging-v02.api.letsencrypt.org/directory' type: "cloudflare" # Obtained using instructions above cfapitoken: sometokenMore detail can be found on the upstream Cert-Manager documentation for Cloudflare.
Route 53 DNS Provider
To be completed
Akamai DNS Provider
To be completed
Digital Ocean DNS Provider
To be completed
Configure Ingress using clusterissuer
Here’s an example on how to add ingress to a chart with clusterissuer for a single domain only.
ingress: main: enabled: true integrations: traefik: enabled: true middlewares: - name: auth namespace: traefik certManager: enabled: true certificateIssuer: domain-0-le-prod hosts: - host: librespeed.example.comVerifying clusterissuer is working
Once installed using the Ingress settings above, you can see the kubectl events for the chart in question to pull the certificate and issue the challenge directly. See the example below:
Renewals are handled automatically by clusterissuer.